Layers of Protection in Business Security Systems

A layered approach to protecting assets isn’t a new idea, but new technologies can improve its implementation.
Anyone who has seen Ocean’s Eleven understands that several layers of security protect high-value assets. It’s an excellent way to keep things protected. While a safe or locked drawer protects valuables, several layers of protection surround that safe, making it nearly impossible to penetrate.
Before Danny Ocean—or any other potential threats—can gain access to your assets, he must pass through several layers of progressively stronger security. Each layer makes it that much more likely that potential threats will be detected and eliminated.
The origin of this model is difficult to trace, mainly because it has been around for so long. The Transportation Security Association (TSA) released a video outlining its layers of security in 2017. Cybersecurity experts have adapted the idea of layered security to cybersecurity. Even medieval castles in Europe, which are hundreds of years old, demonstrate layered security in their use of moats, drawbridges, watchtowers, thick inner and outer walls, and limited access to valuables. Asset protection professionals today sometimes look to medieval castles as inspiration for modern security designs.
This model of using multiple layers of security is simple enough to understand but can be complex in execution. Here we’ll discuss each layer of protection, what it looks like in different security contexts, and what technologies exist to make each layer of security stronger.
Layers of Physical Asset Protection
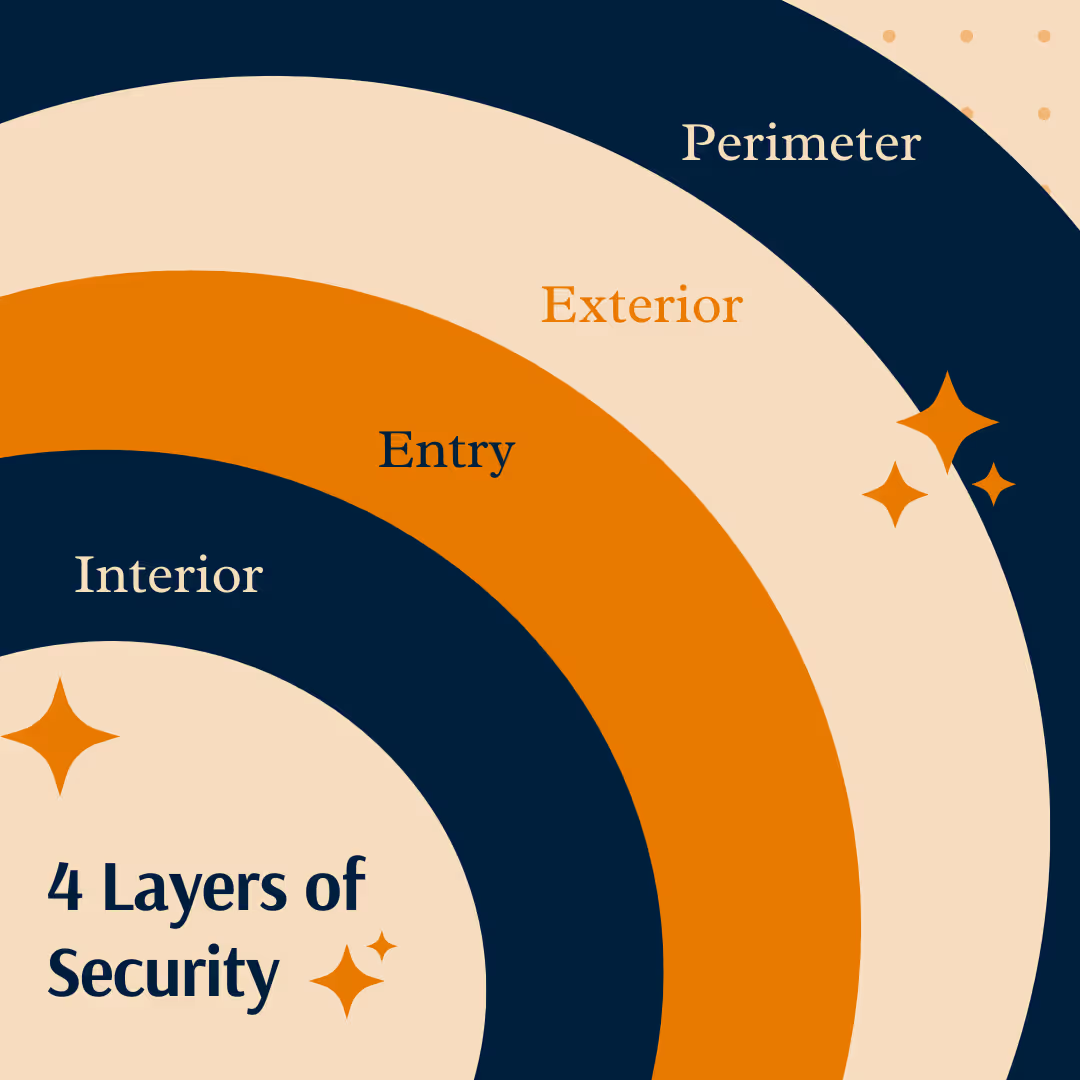
Generally speaking, there are four layers of security: the perimeter, the exterior, the entry, and the interior. The perimeter is outside the protected area—in a home, this would be your property line. The exterior is outside the building but inside the protected area—a parking lot, for example. The entry is the area surrounding the protected goods, like a shared office space or the interior of a home. Finally, the interior is the smallest area that encompasses the protected assets. This small area could be a bedroom in a house or something even smaller, like a locked filing cabinet or a safe. The illustration above is a simplified representation of layers of security.
It’s easy to apply the four levels of security to physical spaces, but professionals in cybersecurity, travel security, asset protection, home security, and more can all use these principles to prevent crime.
Perimeter
In physical properties, protecting the perimeter can be as simple as putting up a fence or as complex as choosing a remote, hard-to-reach location for your home. In cybersecurity, it might be a firewall.
Security technologies that make protecting the perimeter easier include cameras, electronic access gates, electric fences, and identity badges.
Exterior
Once a potential threat has breached the perimeter, more obstacles await at the exterior. In some places, security guards protect exterior areas by ensuring that only authorized personnel enter a building. Cybersecurity at the “exterior” might include authentication via username, password, or biometric security.
In some ways, security at the exterior level can be similar to protection at the perimeter. In medieval castles, inner walls and outer walls were similar—the inner wall, like the outer wall, was sometimes protected by a second moat and drawbridge. Security at this level aims to make it simple for the right people to pass through but complex for potential thieves, who are more likely to be caught when they attempt to breach the wall again.
Entry
At the entry point, potential threats face more robust security than ever before. If you think of an office building, this is where a person enters a shared office space. To get here, they have passed cameras, security guards, entry checkpoints, and several workers.
Security at this point might include:
- A locked office door
- A visitor log that records when outsiders come and go
- A personal assistant who protects a person’s time
- Office workers who would be witnesses to potential crimes
In cybersecurity, this might look like encryption. Encryption ensures that, even if hackers access data transfer information, they can’t read it.
Interior
The interior contains the most valuable assets and, therefore, has the most advanced protection. In movies, this is where lasers that detect movement surround a locked vault. In homes, it’s the locked file cabinet or the gun safe. In banks, it’s the vault that contains the cash. In digital security, this is where the most sensitive information is stored.
Many of the same security technologies may be helpful here that were useful in other areas. For example, the royal family’s sleeping quarters were often inside the inner wall and in a high tower with only one access point, protected by armed guards. Security at your interior level operates similarly. It might involve locks, passwords, biometric security checks, key cards, passcodes, or other security technology.
Things to Consider
As you implement a layered approach to asset protection in your work, consider which technologies provide high-quality, measurable protection and which offer little more than you already have. Of course, when making significant investments, it’s also essential to consider cost, maintenance needs, and longevity. But in all cases, investing in security is an excellent way to ensure you, your employees, your customers, and your assets stay safe.

%20(1).avif)

